Nuclear power plants have the strictest security requirements in the world. These requirements have prevented cutting edge and cost effective solutions in the past, but no longer. Our solutions bring new features and functionality that will improve the performance of security operations by allowing for faster assessment, detection, and interception of threats while simultaneously reducing capital and O&M costs compared to industry competitors.
Our team is comprised of industry experts who have deployed hundreds of different products and solutions for thousands of customers across numerous mission critical verticals. We act as extensions of your security and engineering departments to remedy or stay in front of your most complex challenges.
FEATURE HIGHLIGHTS
“Protected Area” and “Owner Controlled” security computer systems
CCTV: Analog, HD over Coax, Secure IP, Thermal, PTZ w/ slew to cue and adversary auto-tracking
Gates and Turnstiles
Perimeter security and intrusion detection systems:
- Microwave
- Fiber
- Coaxial
- Passive/Active Infrared
- Radar and Lasers
High security badging systems:
- Smart Cards (HSPD-12, FIPS 201)
- Biometrics: Hand Geometry, Fingerprint, Face, and Iris
Drone patrol and assessment
BENEFITS
Security and Vulnerability Assessments
Conceptual Design
Product Viability Studies
Specification Writing
Project Management
Quality Control
Factory and Site Acceptance Testing
Onsite Installation
Next Generation Security Applications
Our security computer systems have been carefully vetted against the most stringent of security regulations to ensure they meet industry requirements. More importantly is what they can do above and beyond current industry offerings. Security applications have made significant strides in performance, serviceability, usability, and function.
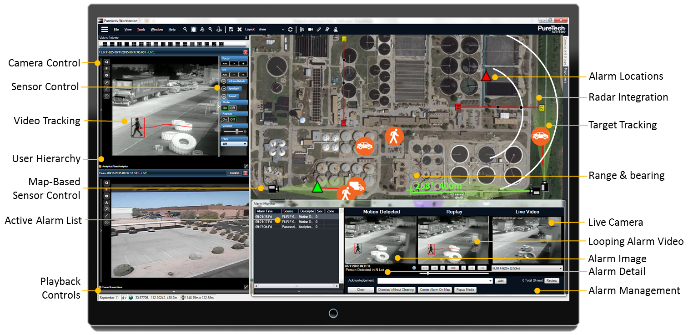
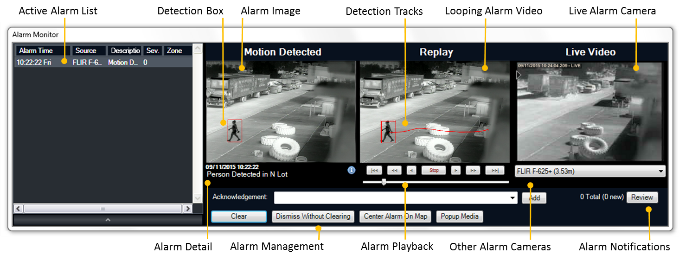
Our system provides unparalleled geospatial technology is uniquely aligned for protection of wide area perimeters based on its’ ability to detect, classify, and track targets at long range and in varied environments. The map-based user interface provides ease of operation and advanced wide-area situational awareness. The solution excels at providing security professionals with a comprehensive birds-eye view and management of their security situation.
Key Features
Open and flexible API
Our API lets you, other systems, and third party applications interface directly with our application for a variety of custom integration use cases.
Extensive triggers and macros
Link practically any system object or event with panel-based or host-based triggers and macro functions. Control the system with time schedule events, card access events, alarm events, etc. With this feature the possibilities for automated actions are endless.
Infoready design
InfoReady design allows for easy access to all of your system data. Built-in reporting provides quick results on personnel, access, door status, and event history.
Quick reports with trace history
Get immediate reports on who is going where with trace history. Click anywhere in the application for fast information – right at your fingertips.
Drag and drop throughout
Streamline all tasks – throughout the entire application – with drag and drop functionality. Drag access levels to new cardholders, filter events by dragging a device to the event summary, drag monitor points to output creating instant I/O links.
Next Generation System Architecture
To meet the demands of ever changing requirements, including ongoing vulnerability management, we supply a “modern security system architecture” that is modular, scaleable, upgradeable, and serviceable. Based on current trends in hyper-converged infrastructure, our system architecture will prevent you from ever having to perform a full turnkey upgrade ever again.